You can hide files on any operating system, but hidden files can be accessed by anyone with access to your PC or its storage. Encryption actually protects your files, preventing people from accessing them without your encryption key.
Even if intelligence agencies could bypass this encryption — and we’re pretty sure they can’t — it’s still useful. Encryption can protect sensitive financial, business, and personal data from people with access to your hardware.
Windows
RELATED:What Is Encryption, and How Does It Work?
Working with AES Crypt for file encryption is very easy, in windows, you can easily encrypt a file just by right clicking and choosing the option of AES Crypt to do its task. In MacOS you can just drag and drop the file into the software area and it will do the rest by itself. Best encryption software, free download - Encryption Buddy, Easy Encryption, MEO Free File Encryption for Mac, and many more programs.
Windows has built-in BitLocker encryption. BitLocker drive encryptio ncan encrypt your entire Windows system drive or another internal drive. BitLocker To Go can encrypt a USB flash drive or another external media device. BitLocker can also be used with a VHD file, creating an encrypted container file that contains encypted files. BitLockeris only available on Professional, Enterprise, and Ultimate editions of Windows. It’s not available on the standard editions of Windows, like Windows 7 Home or the “core” edition of Windows 8 or 8.1.
New Windows 8.1 computers also offer “device encryption”, but this requires specific hardware and the use of a Microsoft account that backs up your encryption key online. This is a very limited encryption feature, but at least it works on every edition of Windows!
Since you probably can’t use BitLocker, you’ll need a third-party encryption solution on Windows. TrueCrypt was previously the encryption solution nearly everyone recommended. It offers a variety of encryption methods, so you can encrypt your entire system drive, encrypt a removable drive, or just create an encrypted container to encrypt some specific files.
Unfortunately, TrueCrypt’s status is now uncertain. On May 28, 2014, the TrueCrypt project’s website was replaced with a messagesaying TrueCrypt is no longer maintained and is unsafe to use. TrueCrypt’s website recommends you use BitLocker on Windows instead. However, an audit of TrueCrypt’s code has found no serious problems. The Gibson Research Corporation site maintains a page with the final releases of TrueCrypt you can download and use. They argue that it’s safe to use.
Is TrueCrypt really safe to use? Well, we don’t really know — there’s a lot of debate and uncertainty here.
RELATED:How to Password Protect Files and Folders With Encryption
No other free, open-source encryption tools are as polished on Windows. TrueCrypt was the tool everyone had congregated around. However, you can still use other tools. For example, 7-Zip and other file-archiving tools include built-in encryption. You can use 7-Zip to create an AES-256-encrypted archive file you need a password to open. This solution won’t let you encrypt an entire hard drive, but it will let you encrypt a few files.
Linux
Ubuntu includes built-in support for encryption, and so do many other Linux distributions. Encryption features are available to all Linux users. For example, Ubuntu allows you to encrypt your system while installing it. Ubuntu and other GNOME-based Linux distributions also allow you to easily encrypt removable drives with the Disk Utility application.
Linux offers many other encryption tools. For example, you can also use encfs to encrypt files in any other folder. The graphical Archive Manager tool can easily create encrypted archives. The examples here are all for Ubuntu, but these methods are similar on many different Linux distributions and desktop environments. Perform a search to see what encryption tools your Linux distribution of choice includes.
Mac OS X
Apple’s Mac OS X also includes a variety of built-in encryption features. There aren’t different editions of the Mac OS X desktop with different included software, so these encryption tools are available on every Mac.
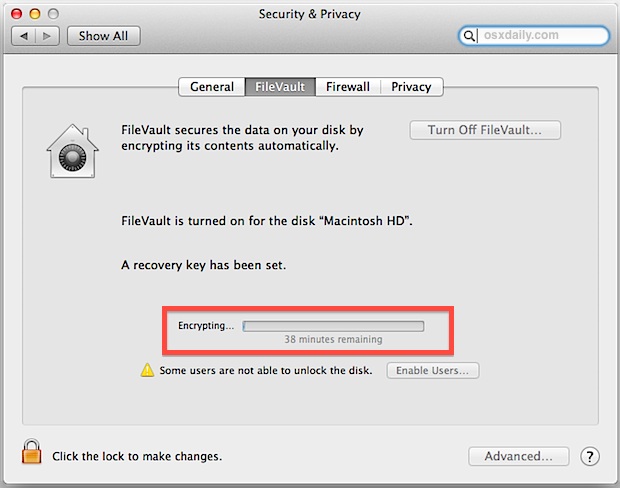
FileVault allows you to encrypt an entire system drive. You can also quickly encrypt a removable drive from the Finder — you’ll see an encryption password prompt when you plug it into a Mac in the future. The Disk Utility allows you to create an encrypted disk image file you can lock and unlock on demand. All of these features are built-in and can set up and used with a few clicks.
Encryption is a complex topic. Whatever encryption scheme you choose to use, be sure to set a strong passphrase. Encrypting your files with a weak passphrase will make them easy to decrypt in the future.
READ NEXT- › What Should You Do If You Receive a Phishing Email?
- › Why Do You Have to Log In to Your Home PC, Anyway?
- › The Best New Features in Android 10, Available Now
- › How to Use the chown Command on Linux
- › What’s New in Windows 10’s 20H1 Update, Arriving Spring 2020
Best Encryption Software 2019 - Encrypt Files on Windows PCs
We spent more than 60 hours testing and reviewing encryption software. We believe Folder Lock is the best encryption software overall because it is very secure and easy to use, plus it includes a password recovery feature. It also has extra privacy features, like a file shredder, stealth mode and a virtual keyboard. If you’re a Mac user, we suggest you use Concealer to encrypt your files. And if you need to use encryption programs on more than one computer, Secure IT is the best value because it comes with multiple user licenses.
Best OverallFolder Lock
Folder Lock is our top pick for encryption software because it makes both encrypting and decrypting files easy, works fast and uses the very secure 256-bit AES algorithm..
Best ValueSecure IT
Secure IT compresses files while securing them and uses the most secure encryption algorithm to protect your information. It comes with three user licenses, making this program the best deal.
 Best for Mac
Best for MacConcealer
Concealer is compatible with Mac, uses the strongest encryption algorithm available and compresses your files as it secures them. It also comes with a password generator and a password strength meter.
| Product | Price | Overall Rating | Performance | Security | Minimum Number of Devices | Speed | Ease of Use | File Compression | File Shredder | Password Generator | Password Strength Meter | Password Recovery | Encryption Algorithm Type | Self-Extracting Files | Stealth Mode | Windows 10 | Windows 8 | Windows 7 | Windows Vista | Mac OS |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Folder Lock | View Deal | 4.5/5 | 4.9 | 5 | 1 | 1 | 1 | 0.9 | ✓ | ✖ | ✓ | ✓ | 256-bit Key AES | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✖ |
| Secure IT File Encryption | View Deal | 4.5/5 | 5 | 3.4 | 3 | 0.85 | 1 | 1 | ✓ | ✖ | ✓ | ✖ | 256-bit Key AES | ✓ | ✖ | ✓ | ✓ | ✓ | ✓ | ✖ |
| Concealer | View Deal | 4.5/5 | 4.7 | 4 | 1 | 0.77 | 0.9 | 0.96 | ✓ | ✓ | ✓ | ✖ | 256-bit Key AES | ✖ | ✖ | ✖ | ✖ | ✖ | ✖ | ✓ |
| Renee File Protector | View Deal | 4.5/5 | 4.5 | 5 | 1 | 0.9 | 0.9 | 0.8 | ✓ | ✖ | ✓ | ✓ | 256-bit Key AES | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✖ |
| Kruptos 2 for Windows | View Deal | 4.5/5 | 4.4 | 4 | 2 | 0.9 | 0.8 | 0.8 | ✓ | ✓ | ✓ | ✖ | 256-bit Key AES | ✓ | ✖ | ✓ | ✓ | ✓ | ✓ | ✖ |
| SensiGuard File Encryption | View Deal | 4.5/5 | 4.2 | 5 | 1 | 0.7 | 0.6 | 1 | ✓ | ✖ | ✓ | ✓ | 256-bit Key AES | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✖ |
| CryptoForge Encryption Software | View Deal | 4.5/5 | 4.5 | 4 | 1 | 0.75 | 0.9 | 0.9 | ✓ | ✖ | ✓ | ✖ | 256-bit Key AES | ✓ | ✖ | ✓ | ✓ | ✓ | ✓ | ✖ |
| File Encryption XP | View Deal | 4/5 | 4.3 | 4 | 1 | 0.77 | 0.9 | 0.96 | ✓ | ✓ | ✖ | ✖ | 384-bit Key AES | ✓ | ✖ | ✓ | ✓ | ✓ | ✓ | ✖ |
| Advanced Encryption Package 2017 | View Deal | 4/5 | 4.4 | 4.5 | 1 | 0.8 | 0.7 | 1 | ✓ | ✓ | ✓ | ✖ | 256-bit Key AES | ✓ | ✖ | ✓ | ✓ | ✓ | ✓ | ✖ |
| Espionage 3 | View Deal | 4/5 | 4.3 | 2.9 | 1 | 0.74 | 0.9 | 1 | ✖ | ✖ | ✓ | ✖ | 256-bit Key AES | ✖ | ✖ | ✖ | ✖ | ✖ | ✖ | ✓ |
Best Encryption For Mac
Best Overall
Folder Lock
We picked Folder Lock as the best encryption program because it is easy to use, includes the best security features and has plenty of tools to protect your sensitive information. It costs a bit more than other programs, but it also has a lot more features.

To encrypt files, you simply drag and drop them into Folder Lock, but you can also right click on the file you want to encrypt and see an option to secure it using Folder Lock. It took less than six seconds for the program to scramble our test files. While we only encrypted 128MB of data, it would only take a few minutes to secure several gigabytes. Once your files are encrypted, the program hides them so anyone who connects to your computer remotely or hacks into your system can’t see them. Also, Folder Lock uses the highest encryption algorithm available.
Folder Lock includes a file shredder, virtual keyboard and password strength meter, which helps you create strong passwords to your files. It is one of the only programs we reviewed that lets you recover your passwords if you forget or lose them – with other software, if you lose your password you lose your encrypted data.
Best Value
Secure IT
Secure IT is inexpensive, comes with three user licenses and securely encrypts your data.
It compresses files as it encrypts them making them 3 percent smaller. This makes them slightly easier to share in emails or save to USB drives.
While it isn’t the fastest program we reviewed, Secure IT only took about 20 seconds to scramble our 63 test files. You can create self-extracting files, including those in EXE, RAR and ZIP formats, using Secure IT. These aren’t secure like encrypted files, but this feature makes it easy to compress less sensitive data, or share secured information with others that don’t have a deciphering program on their computer.
The program’s files shredder destroys any type of files. You choose the number of passes the files make through the shredder – the more passes they make, the less likely hackers are to find any track of the information. Secure IT is compatible with all versions of Windows including Vista and XP.
Best for Mac
Concealer
Concealer is designed specifically for Mac computers, and while it takes longer to encrypt files than other programs do, it compresses them as it encrypts to free up storage space on your computer.
This Mac encryption software performed well in our ease of use tests, and we were impressed with the number of file formats it can encrypt, including text files and tax forms. You can create categories and save encrypted files under them to keep your information organized. Also, you can customize and attach a card to each encrypted file so you know what it contains without decrypting it first. You have the option to secure the whole database with a master password, or you can secure each card file with its own unique pass key.
Because Concealer is a Mac program, it doesn’t have as many security features as those compatible with Windows. For example, it doesn’t have a file shredder or a password recovery option. It also doesn’t let you create less secure self-extracting files like EXE, RAR or ZIP. However, Concealer encrypts your files using the most secure 256-bit AES key and includes both a password generator and a strength meter, which helps you create passwords that are difficult for hackers to figure out.
Stealth Mode
SensiGuard File Encryption
SensiGuard uses the most secure algorithm available to encrypt and secure your files, and it’s one of the few programs we tested that runs in stealth mode.
This means it hides encrypted files on your computer and will hide itself so someone working on your computer after you won’t have any idea you are using an encryption program. This is especially helpful if your computer is hacked since neither the program nor your secured files will be seen. This software also includes a password strength meter and a secure file shredder. SensiGuard is one of the more difficult programs to use, and it takes longer than most encryption software to secure files. However, we were impressed that, despite the wait time, this program automatically compressed our files by an impressive 97 percent during the encryption process.
Best File Encryption Software Review
Password Recovery
Renee File Protector
Renee File Protector’s best feature is it gives you a way to retrieve passwords that you have forgotten.
Most encryption programs exclude this option for the sake of security, but that also means if you forget your password you’re out of luck. Renee gives you the ability of setting up a password recovery option just in case. Plus, it tells you if a password you’ve chosen is a little too easy to figure out. You can hide encrypted files on your computer, so they can’t be seen by anyone who sees your computer, including hackers that sneak in. Unfortunately, Renee File Protector doesn’t compress files during the encryption process, which would save room on your storage drive. But it doesn’t bloat your files either.
Why Trust Us?
We have been testing computer security and privacy programs for over 15 years. When we review encryption software, we consult with experts in the computer security industry as well as businesses that use encryption software daily, including those in healthcare, education and government industries. Their expert knowledge and experiences, as well as our own in-house tests, help us understand the many uses of encryption software, security levels and requirements, and the tools to look for when choosing a program.
One expert we spoke with is Marjorie Smith, a medical service software administrator for a Virginia-based company that assists doctors, hospitals and clinics with medical billing. Because personal medical information is communicated, both in-office and electronically, Smith and her team are bound by the Health Portability and Accountability Act, or HIPAA, laws and regulations.
Smith explained that HIPAA requires any information that is sent electronically regarding a patient must first be encrypted. Smith also explained that since IT personnel can connect to her computer remotely, files and documents stored on her computer must be encrypted.
One important feature Smith says is essential is a password recovery feature. Because HIPAA requires workers to change their passwords for programs used for storing or sending patient information several times a year, including encryption software, it’s easy to forget passwords. If you don’t have a good IT department at your disposal, which isn’t included with encryption software, a password reset feature is essential.
How We Tested?
We tested each program by encrypting 63 files – a total of 128MB of data saved on Windows computers or 134.5MB on Mac machines. We chose programs that encrypted quickly and integrated well with our computers’ operating systems. And while some programs offer a less secure, free program, we tested the premium versions to get a feel for all the security features available.
Encrypting such a small batch of files only took seconds in most cases. However, some programs took minutes to finish the job. In each case we took our results and used them to determine the average time it would take each program to encrypt 1GB of information. Speed isn’t a big deal when you’re locking up a few megabytes of data, but if you’re encrypting gigabytes, a slow program could leave you waiting for hours.
We clocked decryption speed and found that most programs let you access your files quickly. However, in the case of SensiGuard, we had to wait more than six minutes for both encryption and decryption.
Some of our testing included evaluating the security features of each program, particularly those involving passwords. We ranked products based on if they only require a single master password, or let you assign a unique password to each encrypted file. We also looked for password generators and strength meters. A useful feature that most programs don’t include is a password recovery option that helps you still access your files even if you forget your password. We gave extra credit to encryption programs that include this unique, but important function.
How Much Does Encryption Software Cost?
Most encryption software costs about $40 and can be used on multiple devices. If it only comes with one user license, look to see if it includes self-extracting files. This allows you to send encrypted files to another user or to yourself through email and open it on another device that doesn’t have the same program installed on it. Usually this is done by providing the receiver with a password that unlocks and decrypts the file.
Can I Encrypt an External Hard Drive?
You can encrypt an external drive, or thumb drive, using encryption software. The process is the same as if you’re encrypting files and documents on your computer. You have to select the data you want to encrypt and send it through your encryption software. You will be asked to set a password or keycode in order to unlock and decrypt the information in the future.
It is important to note that your external drives, including flash drives, must be encrypted separately from your computer. Just because you’ve encrypted your computer doesn’t mean connected external drives are encrypted as well. As with computer encryption, if you plan to share your encrypted files with a third party that doesn’t have the same encryption program installed as you do, make sure to choose encryption software that includes the option of use self-extracting files. This allows others to unlock secured files with a provided password without requiring an encryption program to be installed on their end first.
Key Features of Encryption Software
Version Compatibility
If your computer runs an older version of Windows, such as Vista or XP, make sure the encryption program supports your operating system. On the flip side, you need to make sure you choose software that has changed with the times and supports the latest versions of Windows, including 8 and 10.
While all the programs we tested are compatible with every version of Windows, we feel that SensiGuard is a good choice for older computers because it only has the most essential tools and won’t bog down your old PC. Plus, it is easy to move to a new computer if you choose to upgrade. However, it takes a while to encrypt and decrypt files.
If you have a Mac computer, you need a program that is designed specifically for that operating system – none of the programs we tested are compatible with both Windows and Mac machines. We believe Concealer is the best option for Macs, but Espionage 3 is also a good choice.
Mac encryption software doesn’t have as many extra security features as Windows programs. They typically lack virtual keyboards, self-extracting file creators and password recovery tools. Mac programs also take a lot more time to secure files compared to Windows software.
Security
Encryption software uses different types of ciphers to scramble your data, and each has its own benefits. Advanced Encryption Standard, or 256-bit key AES, is used by the U.S. government, including the National Security Agency (NSA), and is one of the strongest ciphers available. It scrambles each bit of information. Blowfish and its newer version, Twofish, are encryption algorithms that use block ciphers – they scramble blocks of text or several bits of information at once rather than one bit at a time.
The main differences between these algorithms are performance and speed, and the average user won’t notice the difference. Blowfish and Twofish can’t encrypt large files, so if you need to secure gigabytes of data, use AES encryption. Blowfish and Twofish algorithms are considered practically unbreakable, though given enough time and computing power, both could theoretically be broken.
AES has long been recognized as the superior algorithm and is required for financial institutions, schools, government agencies and healthcare facilities that deal with sensitive personal information. Because of this we preferred programs that use it and ensured these were included in our final choice of the best encryption software.
When Is a Free Program Enough?
Many free file encryption programs exist, and they might be strong enough for your needs. We tested VeraCrypt and Windows’ built-in encryption solution BitLock. These are bare-bones programs that allow you to protect your files and nothing else – they don’t have a file shredder, password generator or password strength meter. Also, these applications are less intuitive than their for-pay counterparts. The paid versions walk you through every step and have easy-to-read help files and tutorials.
So, if you’re comfortable and familiar working with certificates and keys to encrypt files, BitLocker may work well for you. VeraCrypt’s system encrypts in volumes and allows you to create a hidden, encrypted volume within another encrypted file.
Encryption For Mac
All-In-One Security & Norton Security Premium
Just like there is a place for free encryption software, there is a time when an all-in-one security program is the best solution for you. Norton Security Premium is the best computer protection program available, and we’ve physically tested it with live internet threats to make sure it works as it claims. Norton Security blocks malware, including ransomware, rootkits and viruses, from infecting your computer. It includes spamware to keep harmful messages from hitting your email inbox, and has a powerful firewall to keep hackers and snoops out of your system. Norton Security Premium also includes encryption tools and secures your files with the highest, AES 256-bit key algorithm.